Hi 👋, I'm Anshumaan Singh
I build security control planes across CI/CD, artifact integrity, Kubernetes runtime guardrails, and cloud governance so that insecure paths become operationally hard and secure delivery becomes the default.

🔥 About Me (Security Systems Engineering)
I design and implement secure-by-default delivery systems where security is treated as a platform property, not a manual review step. My work focuses on building non-bypassable controls across source governance, CI/CD verification, artifact integrity, Kubernetes runtime guardrails, and cloud governance boundaries.
I optimize for outcomes that hold under attacker behavior: least privilege enforcement, drift resistance, tamper-evident artifacts, deterministic security gates, and audit-ready evidence that moves with the release from Dev → UAT → Prod.
⚖️ Engineering Philosophy
Shift Smart, Not Just Left
Security should be abstracted into the platform. If the paved road is secure, teams ship faster with less risk.
Identity is the Control Plane
Network boundaries are porous. Strong workload identity + OIDC federation enables keyless, verifiable trust.
Guardrails over Gates
Guardrails preserve velocity while preventing catastrophic failures. Enforce safety without blocking delivery.
Detection as Code
Alerts must map to response playbooks. If an alert has no action, it becomes noise and reduces trust.
🛠️ Implementation (What I actually built)
This is the execution layer — real pipelines, real controls, real enforcement. Not slideware.
CI/CD Security Control Plane
- Engineered multi-stage DevSecOps pipelines enforcing security at build → scan → deploy → validate stages.
- Implemented PR-only merges + CODEOWNERS approvals + branch protections to eliminate bypass paths.
- Standardized dependency graph: verify → build → tag → scan → push → deploy → post-deploy validation.
- Integrated Slack notifications with build metadata (commit, author, workflow run, status).
- Stored scan results as pipeline artifacts to support audit trails, RCA, and compliance evidence.
Supply Chain Integrity + SBOM
- Enforced immutable image versioning (v1.0) and removed “latest” to eliminate deployment drift.
- Built controlled promotion workflow: QA promotes scanned images Dev → UAT → Prod (no rebuilds in prod).
- Ensured only approved + scanned digests are eligible for deployment via registry path enforcement.
- Created evidence chain: scan outputs + approvals + image digest tracking.
Kubernetes Runtime Guardrails
- Implemented kubeaudit checks to detect risky workload patterns and enforce baseline hygiene.
- Standardized secure deployment baseline: probes, limits, safe defaults, namespace patterns.
- Reduced runtime risk by preventing privileged workloads and unsafe configurations.
AppSec + Secrets Remediation
- Led response for hardcoded Azure storage keys, OAuth secrets, and leaked tokens in repositories.
- Coordinated secure secret rotation without production impact.
- Performed web/API/mobile penetration testing and delivered actionable remediation guidance.
🧠 System Design (Security as a platform property)
I design security like reliability: as a system-level invariant enforced through identity, policy boundaries, deterministic verification, and runtime enforcement.
Core Security Invariants
- Identity is the control plane → short-lived credentials, least privilege, verifiable trust.
- Verification is deterministic → CI gates are non-bypassable and produce evidence.
- Artifacts are immutable → digests + version tags + controlled promotion (no rebuilds in prod).
- Runtime is constrained → policy + RBAC + secure contexts reduce attacker movement.
- Everything is auditable → logs + scan outputs + approvals move with the release.
Design Principles I enforce
- Guardrails over manual reviews.
- Secure paved roads for engineering velocity.
- Risk-based gating (severity + exploitability + probability).
- Policy as code, evidence as artifacts.
- Traceability: commit → build → digest → deployment.
🏗️ Reference Architecture: Secure-by-Default Delivery (End-to-End)
A complete view of how secure delivery is enforced from source to production with evidence and controlled promotions.
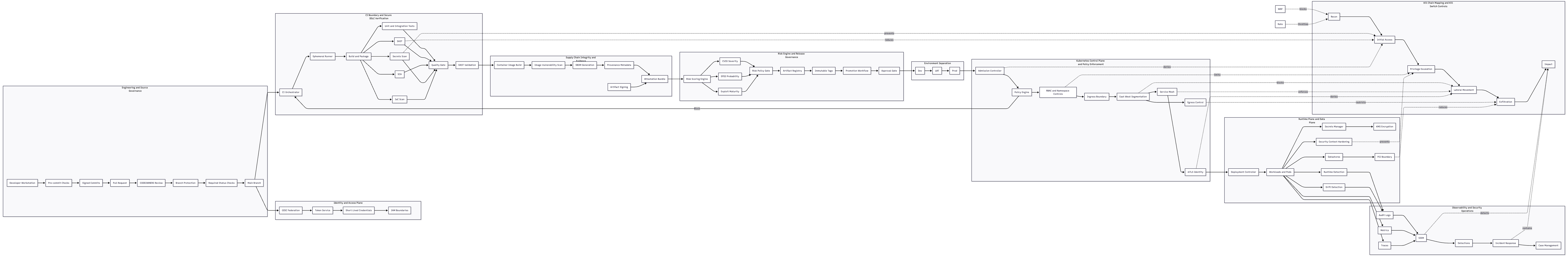
Flow Explanation (No insecure release reaches production)
- Pre-commit checks + signed commits + PR-only merges
- CODEOWNERS + branch protection + required checks
- Main branch becomes single source of truth
- Ephemeral runners execute deterministic security gates
- SAST + SCA + Secrets + IaC scanning enforced
- Quality gate controls pass/fail and stores evidence artifacts
- Build once → scan → generate SBOM → attach provenance
- Image digest tracking + immutability prevents drift
- Evidence moves with release across Dev → UAT → Prod
- Admission policy blocks unsafe workloads before deployment
- RBAC + namespaces reduce blast radius
- Audit logs + SIEM detections + IR playbooks contain impact
📌 Case Studies (Real problems solved)
Real-world security engineering outcomes across pipelines, supply chain, and Kubernetes delivery.
Secrets Leakage Response
- Detected hardcoded Azure Storage keys + OAuth secrets in repos and validated exposure scope.
- Coordinated secure rotation and remediation without production downtime.
- Implemented prevention guardrails: secret scanning + branch protections + required checks.
- Outcome: reduced recurrence through enforcement + governance + audit evidence.
Prisma twistcli inconsistent vulnerability results
- Observed Prisma returning zero vulnerabilities for known-vulnerable base images.
- Cross-validated findings using Trivy + public CVE references to confirm true risk.
- Improved pipeline trust by enforcing scan evidence retention + validation gates.
- Outcome: fewer production pipeline failures caused by scanner inconsistency.
Controlled Promotions (Dev → UAT → Prod)
- Implemented “build once, promote many” model to prevent rebuild risk and drift.
- Added approval gates + registry path enforcement to block unauthorized deployment paths.
- Outcome: digest-level traceability strengthened across environments.
OWASP ZAP DAST with Kubernetes dynamic URL
- Automated DAST using runtime service discovery via kubectl for real endpoint validation.
- Ensured post-deploy security checks reflect production-like behavior.
- Outcome: improved coverage beyond static environment assumptions.
🧨 Threat Model (How attackers actually break systems)
I model threats using attacker behavior, not just compliance checklists. Controls are mapped to kill-chain stages so enforcement blocks real attack paths.
Primary Threat Vectors
- Credential theft (tokens, OAuth secrets, cloud keys)
- Pipeline compromise (runner persistence, secret exposure)
- Dependency compromise (typosquatting, malicious packages)
- Container base image vulnerabilities + drift via latest tags
- Kubernetes privilege escalation (privileged pods, host mounts)
- Lateral movement (east-west traffic abuse)
- Data exfiltration (egress misuse, weak PII boundaries)
Control Mapping (Kill Chain → Defense)
- Recon → WAF + rate limiting
- Initial Access → secrets scanning + SAST + admission deny
- Privilege Escalation → RBAC + securityContext hardening
- Lateral Movement → segmentation + mesh + mTLS
- Exfiltration → egress restrictions + PII boundaries
- Impact → SIEM detections + incident response containment
🧾 Evidence (Audit-ready security delivery)
Proof that controls exist, ran, and produced outputs. Evidence is attached to releases, not stored in memory.
Evidence Pack includes
- Scan outputs: SAST, SCA, Secrets, IaC, Image scan, DAST reports
- Build metadata: workflow run ID, commit SHA, branch, actor
- Artifact metadata: image digest, tags, registry path
- Promotion approvals: QA / release gates / policy decisions
- Retention: artifacts stored per pipeline for compliance and RCA
SBOM Snapshot (Implementation proof)
This image is used as proof-of-implementation artifact.

🧮 Risk Engine (Policy-driven release decisions)
Security gating should reflect exploitability reality. I design release gates using severity + probability + exploit maturity so teams ship safely without unnecessary friction.
Inputs to Risk Scoring
- CVSS → technical severity baseline
- EPSS → likelihood of exploitation in the wild
- Exploit maturity → weaponization / public exploit availability
- Reachability → exposed surface + runtime path
- Compensating controls → RBAC, WAF, egress, segmentation
Policy Gate Outcomes
- Block → exploitable critical vulnerabilities or policy violations
- Allow with evidence → low-risk findings with traceability and audit pack
- Allow with exception → tracked risk acceptance + expiry and follow-up actions
- Auto-promote → clean evidence + approved digest across environments
🏢 Experience (Impact)
Categorized impact points with measurable security engineering outcomes.
CI/CD Security Control Plane
- Engineered a CI/CD Security Control Plane enabling deterministic enforcement across build, scan, deploy, and post-deploy validation stages.
- Implemented PR-only merge governance with CODEOWNERS enforcement, branch protections, and required checks to eliminate direct-to-main release risk.
- Built multi-language SAST coverage for JavaScript/HTML and standardized scan artifact retention for audit evidence and RCA workflows.
- Implemented SCA enforcement for Maven + Node ecosystems with policy thresholds to block high-risk dependency introduction.
- Deployed organization-wide secret scanning controls to prevent leakage of OAuth secrets, cloud keys, and hardcoded tokens across repositories.
- Integrated container vulnerability scanning using Prisma Cloud (twistcli) and enforced cross-validation using Trivy to reduce scanner trust failures.
- Implemented IaC scanning to prevent insecure Kubernetes manifests and cloud misconfigurations from reaching runtime environments.
- Automated OWASP ZAP DAST with Kubernetes service discovery (kubectl-based dynamic URL extraction) for post-deploy validation coverage.
- Standardized pipeline execution order and dependency flow: verify → build → tag → scan → push → deploy → validate → notify.
- Built evidence retention strategy: scan outputs, logs, approvals, and digests retained as artifacts to support compliance and investigations.
- Implemented Slack-based release telemetry with commit/build/author context to improve engineering visibility and reduce release ambiguity.
- Optimized pipeline execution using parallel scanning stages while preserving enforcement integrity and coverage.
Supply Chain Security + SBOM + Attestation
- Implemented controlled artifact promotion workflow where QA promotes images separately for UAT/Prod (no rebuilds in prod).
- Enforced immutable versioning (v1.0) and prevented use of latest tags to eliminate deployment drift.
- Ensured only scanned + approved images are eligible for deployment using digest-level validation patterns.
- Built evidence model: scan results + approvals + image digest tracking = attestation-ready delivery.
- Strengthened traceability from commit → build → image digest → deployment across environments.
- Added promotion gates to prevent deploying images not present in approved registry paths.
Kubernetes Security Engineering
- Implemented Kubernetes security checks using kubeaudit to detect risky cluster/workload configurations.
- Reduced runtime risk by preventing privileged workloads and unsafe patterns via baseline enforcement.
- Standardized secure deployment baselines: probes, limits, safe defaults, namespace patterns.
- Assisted in Kubernetes cluster setup and validation using kubeadm (v1.28.1).
- Improved blast radius control through workload boundary checks and least privilege patterns.
- Mapped runtime risks to enforcement and operational response expectations.
Cloud Governance + Migration Security
- Supported secure cloud governance strategy across environments and teams.
- Designed secure identity and access boundaries to reduce cloud exposure.
- Worked on GCP migration initiatives and security design for HIPI project.
- Implemented posture improvements aligned with production delivery requirements.
- Supported ingress/CDN exposure patterns and service hardening approaches.
- Built governance as guardrails (policy) instead of documentation-only controls.
AppSec + Secrets Remediation
- Performed web, API, and mobile penetration testing as part of application security responsibilities.
- Identified and validated auth, access control, API misuse, and security misconfiguration issues.
- Supported secure design review and remediation guidance for engineering teams.
- Led response for hardcoded Azure Storage Account keys found in repositories.
- Remediated hardcoded OAuth credentials and leaked secrets across source control.
- Coordinated secret rotation safely without production impact.
- Improved repo hygiene using scanning + governance + enforcement patterns.
- Reduced false positives by tuning policies and aligning severity with exploitability.
- Defined deployment decisions: block/allow based on thresholds and risk acceptance workflows.
- Acted as bridge between AppSec + DevOps + QA + Engineering to ensure secure releases at scale.
🎓 Education
🧩 Projects
Engineering projects that demonstrate secure delivery, automation, and system design.
Netflix Clone — Secure CI/CD Pipeline
- Built CI/CD pipeline with SAST, SCA, secrets scanning, Trivy image scan, and controlled deployment.
- Implemented Slack notifications with build + commit metadata.
- Focused on immutable image tags (v1.0) and evidence retention.
Kubernetes Security Validation Toolkit
- Combined kubeaudit + cluster checks for misconfiguration detection.
- Designed baseline enforcement for risky workload patterns.
- Mapped findings to remediation playbooks for engineering teams.
🧭 Explorer (What I’m building next)
Active areas of engineering exploration: making security controls faster, stronger, and more measurable.
Secure Build Provenance
- Expanding provenance metadata to include environment and runner identity.
- Improving attestations for artifact traceability across Dev → UAT → Prod.
Policy as Code Expansion
- Strengthening policy gates for Kubernetes workload hardening.
- Improving enforcement for registry paths + digest allowlisting.
Risk-based Security Gates
- Reducing false positives by aligning severity with exploitability.
- Tracking risk acceptance and expiry-based exceptions.
Security Metrics & KPIs
- Measuring gate pass rate, mean time to remediate, recurrence of secrets leakage.
- Building dashboards for release integrity and evidence coverage.
🧰 Skills (Security Systems Engineering)
Grouped by real-world engineering domains.
DevSecOps + CI/CD
- GitHub Actions, Jenkins, pipeline orchestration
- Branch protection, CODEOWNERS, PR-only enforcement
- Artifact retention, evidence generation, release governance
Supply Chain Security
- SBOM generation, artifact signing, digest traceability
- Immutable versioning + controlled promotions
- Container security scanning: Prisma twistcli, Trivy
Application Security
- Web/API/Mobile penetration testing
- AuthZ/AuthN testing, misconfigurations, API abuse validation
- Remediation guidance + secure design reviews
Kubernetes Security
- RBAC, namespaces, workload hardening baselines
- kubeaudit-based checks and enforcement patterns
- Ingress exposure and blast radius reduction
🏅 Certifications (Verified)
Clickable cards with verification links.






🏆 Achievements
Verified impact + certifications + security engineering outcomes.
Certifications
- CKS — Certified Kubernetes Security Specialist
- CKA — Certified Kubernetes Administrator
- GCP Professional Cloud Security Engineer
- GCP Professional Cloud Architect
- Terraform Associate
Security Engineering Outcomes
- Implemented security enforcement across 350+ microservices delivery scope.
- Built CI/CD security gates with evidence retention and audit-ready outputs.
- Enabled controlled promotions with immutability and digest-level traceability.
- Reduced secrets exposure risk through scanning + governance + rotation response.